Blog by DE7AULT | linkedin.com/in/morganbrazier | @DE7AULTsec
In short, using Direct Memory Access (DMA) it is possible to silently read and overtly write memory outside the realms of the CPU. This enables for some interesting trickery if your goal is to try and bypass videogame anticheat (AC) software, antivirus (AV) software or endpoint detection and response (EDR) sensors. However, DMA also has incredible potential for applications in the digital forensics field.
What is DMA?
Direct Memory
Access (DMA) is a method of memory retrieval used by hardware to access
memory independently of the CPU, usually via a DMA controller, either
peripheral, i.e., a PCIE card reading from bus or internal, such as your GPU's DMA
controller.
Although there
are multiple types of DMA, for the purpose of this B2600 writeup, we’re only going to
be looking at third-party DMA, more commonly known in the scene as just DMA, or
standard DMA (no many really care about the other types).
DMA
controllers defined by Colorado University:
“A DMA controller is a device, usually
peripheral to a computer's CPU, that is programmed to perform a sequence of data transfers on behalf of
the CPU.
A DMA
controller can directly access memory and is used to transfer data from one
memory location to another, or from an I/O device to memory and vice versa.”
Although the topic of this B2600 blog might suggest otherwise, DMA does have legitimate uses, and you are more than likely using it on a daily basis, most likely due to one or multiple of the following requesting DMA access:
- DRAM (Unheard of)
- HDD (Rare)
- Floppy (lol)
- Soundcard
- GPU (Most common)
Introduction to DMA attacks
Now we know what DMA is, we can start to
look at how to use it to attack a system.
DMA attacks are a type of side-channel
attack perfect for extracting secrets or bypassing platform security, i.e., disk
encryption keys, modifying registry, usually using a peripheral device,
plugged in via thunderbolt or PCI/E or firewire, if that’s your thing.
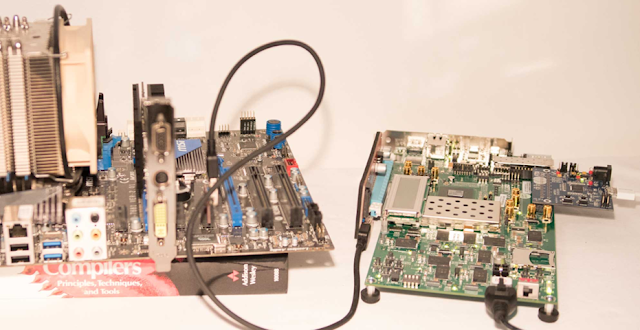
On the other hand, we could try to remotely take over the DMA controller of an existing bit of hardware within the target computer, for this blog we are going to be looking at physical access, and utilizing a peripheral device.
Microsoft showcased a demo in 2023
bypassing Windows 11 biometric security using PCILEECH, a DMA attack framework
developed by Ulf Frisk (the godfather of DMA attacks):
During the demo (in the video above), it is illustrated how straightforward these physical access types of attacks are using PCILEECH, regardless whether the device is locked or not, assuming there is no full disk encryption.
Using PCILEECH we can easily dump the
devices memory, and fish out anything of interest, keys, tickets, anything that
would pass through memory.
We can also read and write memory on the
fly, using this to create a shell via PCILEECH. As you can probably imagine, the
possibilities from here are vast, as you are executing in memory
and never hitting the disk.
Below is an example of a UEFI bootkit implant
dropped via a DMA attack, which will continue to persist on the target system, even after HDD replacement:
Mitigations and bypasses
Even though DMA can exploit an often undefended and wide attack surface, most DMA
attacks can be mitigated by simply enabling virtualization tech BIOS. Most
commonly, VT-d and IOMMU. KASLR previously worked as a defence, but has now had numerous
workarounds appear in the last years for DMA attackers.
Simply blocking associated ports or drivers used by known DMA peripherals (Xilinx, LambdaConcept, Screamer) is also commonly done by anticheat companies. Certain markers in the firmware of these devices cannot be modified without significant effort, including the master abort flag. Knowledge of how to customize this firmware properly is highly sought after within the underground cheating community and often fetches a high price =)